Data sovereignty: what it is and why it matters for your business
Cloud-first data management makes life simpler. You can access data from different locations and you're not responsible for maintaining your own infrastructure. However, it often creates a new kind of complexity when it comes to data handling: your data can be collected in one place, stored in another, processed in a third, and accessed from anywhere.
That matters because data doesn't travel alone. It carries legal obligations, privacy expectations, and security risks with it – especially when you're handling personal data, financial information, or other sensitive data. And while multinational companies have dealt with cross-border rules for years, data sovereignty is now a strategic priority for teams of every size, from market research and HR to healthcare, government, and higher education.
This guide breaks down why data sovereignty should be a consideration for your business. You'll get a clear answer to what data sovereignty is, how it differs from data residency and data localization, what to watch for in major data protection regulations, and the practical steps that make data sovereignty compliance achievable for any business.
What is data sovereignty?
Data sovereignty refers to the principle that data is subject to the laws and regulations of the country or region where it is collected, stored, or processed. In other words, the rules that apply to such data depend on jurisdiction, not just your company's headquarters or your cloud provider's server locations.
A few details make this more than a tidy legal concept:
- Data sovereignty rules apply to more than storage. They can cover data collection, how you process data, retention periods, breach notification, and the rights people have over their own data – an important consideration for survey software providers.
- Cloud computing adds layers. Even when stored data sits in one physical location, it may be accessed, backed up, mirrored, or supported across borders by cloud service providers.
- Government access is part of the picture. In some jurisdictions, local laws can empower law enforcement agencies to request access under specific conditions. Whether that's acceptable depends on your risk profile, your contracts, and the applicable laws.
- Industry is also a factor. Some industries need to observe more rigid regulations, such as HIPAA in the United States, which impacts how healthcare providers handle data.
Data sovereignty usually becomes a key consideration when a team realizes they can't confidently answer basic questions like: "Where does our organizational data reside, which data laws apply, and who can access it?"
That uncertainty is exactly why the next step is clarifying the key differences between sovereignty, residency, and localization – they can get mixed up, and the distinction affects your decisions.
Data sovereignty vs. data residency vs. data localization
Data sovereignty is the legal umbrella. Data residency and data localization are two ways the umbrella shows up in real-world architecture decisions.
Data sovereignty
Data sovereignty pertains to the legal oversight of data based on the regulations of the country where it is generated or processed.
If data generated in a particular region is processed there, local regulations can apply, even if the organization is based elsewhere. Contracts, audit trails, and security measures are just as important as where the servers sit.
Data residency
Data residency refers to the physical location where data is stored, such as a specific data center or cloud region.
It's about geography and infrastructure, and answers questions like: "Which country is the data stored in, and which data centers are used?" Residency can support compliance, but it doesn't automatically guarantee it.
Data localization
Data localization is a stricter rule set. It's the requirement that data generated within a region must remain stored there before any external use or transfer, meaning it can limit your ability to transfer data across borders – even for processing, analytics, or support.
Some regulations create hard constraints around specific data types, such as health records, government data, or national identifiers.
Here's a quick comparison you can use when aligning IT and compliance stakeholders:
These concepts interconnect in practice. You might choose EU data residency to better protect EU citizens' data, but you still need to address data access by support staff outside the European Union, or subprocessors used by public cloud providers.
Now that the definitions are clear, the obvious question becomes: why is data sovereignty important enough to influence architecture, procurement, and governance?
Why is data sovereignty important?
Data sovereignty is a key component of modern data governance because it connects legal reality to technical reality. If you ignore it, the consequences show up in three key places: compliance exposure, security gaps, and trust.
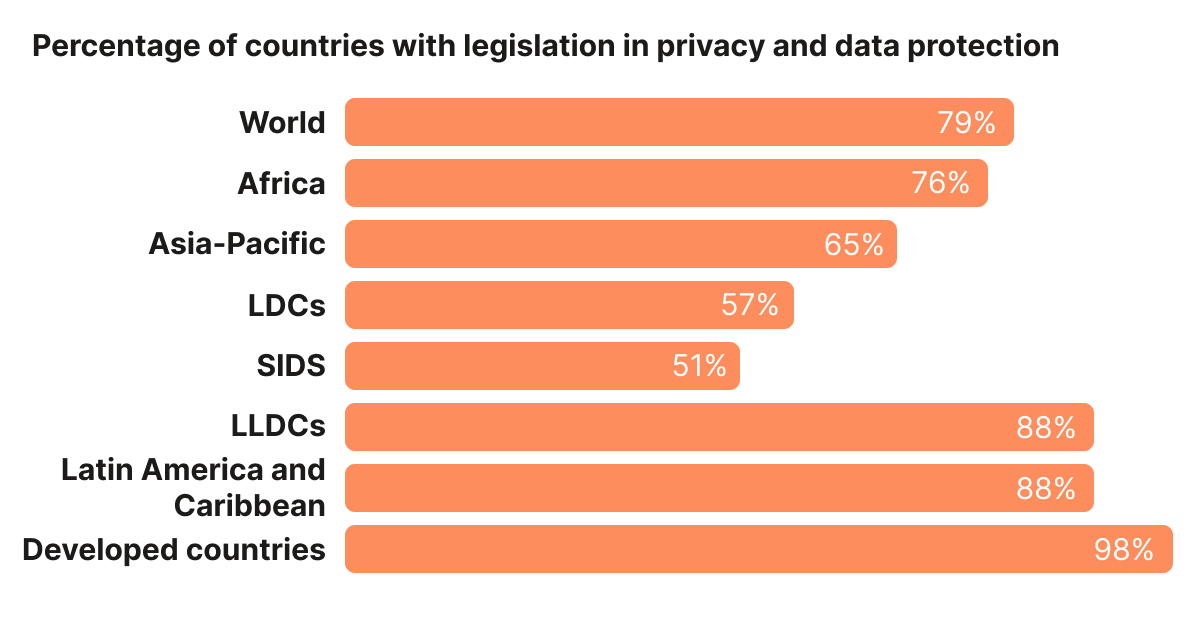
UNCTAD's tracking of privacy and data protection legislation shows how widespread these expectations have become, with a global majority of countries covered by some form of privacy/data protection legislation.
Legal and regulatory compliance
When you operate across multiple countries, you're rarely dealing with one neat rulebook. You're navigating various laws that can overlap, conflict, or change faster than procurement cycles.
The impact is:
- You may need different retention rules for different regions
- Consent requirements can vary across regulatory frameworks
- Cross-border transfers can require specific safeguards or contractual clauses
Noncompliance can also be expensive. Under the EU General Data Protection Regulation (GDPR), administrative fines can reach up to €20 million or 4% of worldwide annual turnover in certain cases.
Security and privacy protection
Data sovereignty requirements often push organizations to tighten data security, not just because it's a good idea, but because it's expected.
A strong posture typically includes:
- Encryption for data storage and transfers
- Role-based access controls to restrict data access
- Audit logging so you can prove who did what, and when
- Clear separation of environments and least-privilege permissions
It also forces more mature thinking about data types. Financial data and health information often trigger additional controls, and even "basic" personal data can become sensitive depending on context.
Building customer trust
Trust is what you earn when you persuade people that you'll handle their data responsibly. Strong data sovereignty strategies help because they show you've thought beyond minimum compliance.
For research teams, that trust can be the difference between:
- Respondents choosing to share honest data or abandoning surveys
- Stakeholders accepting findings or questioning data integrity
- Customers renewing, or seeing you as a risk
Customer trust is also easier to build when you can confidently explain what happens to data after it's collected – which naturally leads to the regulations that shape those expectations.
Data sovereignty and digital services
Most digital services aren't a one-off purchase. You can't switch suppliers when something goes wrong, as you can with physical products, you have an ongoing agreement and relationship with the vendor – especially once your workflows, users, and data are embedded in a platform.
Vendors whose platforms are accessed through the cloud can change pricing, product features, data access models, or even the rules of reach and visibility after you've adopted them.
The practical impact isn't just cost, it can affect your ability to access your own data, keep systems running during disputes, or move to another provider without downtime – especially when big data volumes, proprietary formats, or integrated identity and admin controls are involved.
In Europe, those realities have helped push digital sovereignty from a policy buzzword into active decision-making.
Recent reporting has highlighted how EU reliance on largely US-based cloud ecosystems is sharpening the focus on tech sovereignty and resilience. According to a recent Gartner report, Europe is forecast to treble spending on sovereign infrastructure by 2027, from $6,868 million to $23.1 billion – surpassing North America's $21.1 billion that year.

Some governments are also making visible shifts: for example, France has announced plans to phase out tools like Zoom and Microsoft Teams across government in favour of domestically hosted alternatives, explicitly framing it around sovereignty, security, and control over sensitive data.
At the EU level, even technical initiatives like the EU cloud certification scheme (EUCS) have become politically charged, with debates over sovereignty requirements contributing to delays – a sign that security, compliance, and strategic autonomy are now tightly intertwined.
For businesses, the takeaway is simple: data sovereignty isn't only about the physical location of data stored in a data center, it's also about portability, contractual rights, who can access data under different jurisdictions, and even geopolitics.
And because sovereignty is hard to maintain if you can't realistically move providers, the EU's Data Act includes measures to make it easier to switch between cloud providers and reduce lock-in.
And once you view digital services through that lens, the next step is understanding the concrete laws and regulations that define data sovereignty requirements – starting with the biggest frameworks most organisations encounter.
Key data sovereignty laws and regulations
With the "why" clear, the next step is understanding the laws and regulations that most often drive data sovereignty compliance. You don't need to memorize every clause, but you do need to know what each framework is trying to control.
GDPR and European Union regulations
GDPR is one of the most influential data protection regulations globally because it sets strict expectations for lawful processing, transparency, and individual rights for any company with data that is stored, processed, handled, or accessed in the EU.
At a high level, GDPR emphasizes:
- Valid legal bases for data collection and processing
- Data minimization and purpose limitation
- Strong requirements around security and accountability
- Constraints on cross-border transfers unless safeguards are in place
The enforcement side is also an important thing to keep in mind, especially considering the potential fine levels referenced earlier in this article.
CCPA and US state privacy laws
In the United States, the landscape is shaped largely by state privacy laws rather than one federal standard. The California Consumer Privacy Act (CCPA), as amended by the CPRA, is a flagship example.
The California Attorney General's office summarizes key consumer rights, including opting out of sale or sharing, and additional rights such as correcting inaccurate personal information and limiting use of sensitive personal information.
For businesses, the challenge is scale: if your business operations span multiple states, you may need a compliance model that can flex as new laws arrive and definitions shift.
Other global regulations
Many regions have their own frameworks that affect how data sovereignty work plays out:
- China's PIPL – A comprehensive personal information law with requirements that can apply even to processing outside China in certain circumstances. Cross-border transfer mechanisms are also a major focus, with structured pathways used to legitimize overseas transfers.
- India's DPDP Act – A national law focused on digital personal data and lawful processing.
- Brazil's LGPD – A broad data protection law that covers processing and international transfer.
- Canada's PIPEDA – Rules for how private-sector organizations collect, use, and disclose personal information in commercial activities across Canada.
- Australian Privacy Principles – The APPs are the cornerstone of Australia's privacy protection framework under the Privacy Act 1988.
- Saudi Arabia's PDPL – The PDPL, which came into full effect on September 14, 2024, enforces strict data localization and security measures under the supervision of the Saudi Data & Artificial Intelligence Authority (SDAIA).
Once you see how many regimes and governments can affect one dataset, it becomes easier to understand why understanding which countries have data sovereignty laws is important to any business that wants to trade overseas.
Which countries have data sovereignty laws?
The above bullet points just scratch the surface, so if you're hoping for a short list, the reality is broader: most countries now have some form of privacy or data protection legislation, and new requirements keep emerging.
The IAPP recently updated its Global Privacy Law and DPA Directory, noting that data protection and privacy laws are in effect in well over 140 countries. The details vary by jurisdiction, and "having a law" is not the same as "enforcing it consistently," but the direction is clear.
In practice, teams most often run into strict requirements in specific regions, including:
- The European Union
- China
- Russia (often through data localization-style rules for certain personal data)
- Brazil
For any organization operating internationally, the safest approach is to assume that applicable laws follow your data. That sets up the next challenge: even if you know the rules, implementing them is not always straightforward.
Data sovereignty challenges
Data sovereignty looks clean on a slide in a presentation. In day-to-day operations, it can feel like a moving target with technical constraints.
Common obstacles include:
- Operating in multiple jurisdictions – Different regulations can define personal data differently, set different consent standards, or clash on retention expectations.
- Evolving regulatory landscape – Policies change, guidance evolves, and enforcement priorities shift. If nobody owns the monitoring process, gaps appear quietly.
- Cloud complexity – Public cloud and multi-cloud setups make it harder to prove where data resides, where it's replicated, and who can access it.
- Cost and resource requirements – Mature data governance takes people, tooling, and ongoing audit readiness.
- Business continuity pressures – Requirements don't pause for natural disasters, outages, or urgent operational needs. Your sovereignty strategy has to survive real-world incidents.
The good news is that most of these challenges become manageable when you treat data sovereignty as a program, not a one-time project. That's exactly what the best-practice section is for.
Data sovereignty best practices
If you want data sovereignty compliance that holds up under pressure, focus on repeatable controls. The goal is to be able to explain, prove, and defend how you manage data – even when the answer is complicated.
Start with these building blocks:
- Map your data landscape – Build and maintain an inventory of what data types you collect, where the data is stored, where you process data, and every place you transfer data. Include backups, exports, and analytics pipelines.
- Choose data residency strategically – Pick regions based on your customer base, the particular region's requirements, and the sensitivity of the data. Data residency and data governance need to align, not compete.
- Implement strong access controls – Use least-privilege permissions, role-based access, encryption, and audit logging. Treat privileged access as a separate category with its own approvals and review cycles.
- Vet cloud providers thoroughly – Ask where data centers are, how support access works, what subprocessors are involved, and how cross-border access is handled. "We store in-region" is not the end of the conversation.
- Consider on-premises for maximum control – If you're in highly regulated industries, or you need to guarantee that data never leaves your environment, on-premises deployment can be the cleanest way to meet strict data sovereignty requirements. It also gives you more control over security measures, update timing, and how you integrate with internal systems.
- Stay current with regulatory changes – Assign ownership, set a review cadence, and track changes in the jurisdictions that matter to your business operations.
Checkbox is built for teams that need strong control over survey-based data collection. If you want cloud survey software hosting with regional options, Checkbox allows you to choose where your data is stored, including in the United States, Canada, Europe, and Australia. If your bar is higher, Checkbox also supports on-premises deployment, so you can store data in your own data center.
With these practices in place, data sovereignty stops being a vague compliance goal and becomes a set of operational habits.
Final thoughts
Data sovereignty isn't just about where your data is stored; it's about proving you understand which laws apply, how you protect sensitive data, and how you keep that promise as your systems evolve.
If you collect data across jurisdictions, treat data sovereignty as a design constraint from day one: map your data flows, choose residency deliberately, lock down access, and pick deployment models that match your risk and compliance needs.
If you're looking for a secure way to collect research or operational insights without losing control of your data, try Checkbox. With region-specific hosting options and on-premises deployment, it's designed to help teams meet strict data sovereignty needs while still running powerful surveys at scale. Request a Checkbox demo today.
Data sovereignty FAQs
In cloud computing, data sovereignty is about how cloud storage and processing interact with national and regional laws. Even when a cloud provider offers a region, you still need to understand:
- Where data is stored and replicated
- Where support and admin access occur
- Which subprocessors can touch the data
- What cross-border transfer mechanisms are used, if any
A practical cloud sovereignty strategy often combines regional hosting, strict access controls, contractual safeguards, and clear documentation.
In cybersecurity, data sovereignty means designing security controls with jurisdiction in mind. It's not enough to secure data; you also need to ensure the right laws and oversight apply to how data is accessed, monitored, retained, and disclosed.
That usually includes encryption, identity and access management, audit trails, and controls around privileged access. It also includes planning for lawful requests, since law enforcement agencies may have different powers depending on where data resides and which legal system governs it.
Contact us
Fill out this form and our team will respond to connect.
If you are a current Checkbox customer in need of support, please email us at support@checkbox.com for assistance.




